This is an old revision of the document!
Table of Contents
Mail Server
The Synchronet Mail Server is responsible for incoming and outgoing Internet e-mail.
Incoming
The mail server accepts submissions via the SMTP and ESMTP protocols, by default, on TCP ports 25 and 587.
By default, the mail server does not allow relaying of mail from unauthenticated clients to external mail servers.
The SMTP server supports authentication via the PLAIN, LOGIN, or CRAM-MD5 SMTP-AUTH methods (client chooses).
The SMTP server optionally supports SMTP-TLS sessions.
The SMTP server can service multiple simultaneous incoming sessions and messages, with multiple recipients per message.
The SMTP server also supports the SEND, SAML and SOML commands for delivering instant messages (a.k.a. telegrams) to users of the BBS.
Special Prefixes
Recipient mail addresses can have special prefixes to direct the routing of the incoming mail:
| Prefix | Syntax | Description |
|---|---|---|
| local: | local:<user> | Deliver to local mailbox only, do not forward to external mail/netmail address |
| forward: | forward:<user> | Forward to the destination user's external mail/netmail address |
| sub: | sub:<code> | Post email contents as message on message sub-board (specified by internal code) |
| qwk-id! | <qwk-id>!<user> | Routes to <user> at QWKnet node with specified QWK-ID (may include a full slash-separated route) |
It is sometimes preferred to use an alias (configured in the ctrl/alias.cfg file) to allow the reception of a more “normal” looking email address and route to the Specially-Prefixed address. The following examples allows the reception of email sent to “cnnreport@<yourbbs>” and forwards the message to the message sub-board with the internal code of dove-deb:
cnnreport sub:dove-deb
Special Addresses
Some specially formatted destination addresses (RCPT TO addresses) are recognized and treated specially by the Synchronet SMTP server.
FidoNet
If the system supports FidoNet-style networking (has at least one address configured in SCFG->Networks->FidoNet->Addresses), then incoming FidoNet netmail messages are recognized with one of the following formats:
<name>@f<node>.n<net>.z<zone>.fidonet<name>@p<point>.f<node>.n<net>.z<zone>.fidonet
Example: rob.swindell@f705.n103.z1.fidonet
Note: the .fidonet host suffix is required even if the destination network is an othernet (not technically part of FidoNet proper). This is a “virtual” TLD, no DNS lookup is performed by the mailserver for destination hostnames with this suffix.
Tags
The Synchronet Mail Server recognizes the incoming special address format: <name>#<tag>@<host>
The <tag> is extracted from the address and if it is not found in the data/user/<usernum>.smtpblock file, the mail message is
sent to the destination user. If the tag matches a line in the .smtpblock file, the email is rejected by the mail server with a “no such user” error.
This feature allows you (the sysop) to easily create and use “temporary” email addresses without requiring additional user accounts. Once you start receiving spam with a tag, just disable that tag by adding it to your .smtpblock file.
Anti-SPAM
The Synchronet SMTP Server contains several anti-SPAM measures:
- DNS-based blacklist (DNSBL) look-up support with exemptions and multiple possible actions upon positive results
- Email address filtering with wildcard support (
text/email.can) - Message subject filtering with wildcard support (
text/subject.can) - Configurable SPAM bait list (
ctrl/spambait.cfg) for auto-blocking mail servers based on honey-pot destination email addresses - Synchronet's normal host filtering (via
ip.canandhost.can) and configurable LoginAttempt tracking/throttling/blocking (insbbs.ini) is also employed
DNSBL
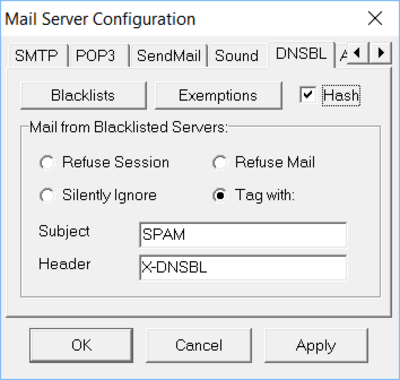
DNS-based Blacklists (DNSBL) are 3rd party databases of IP addresses whose hosts are suspected of being habitual spammers or have other security problems which make mail received from these systems highly suspicious. Different DNSBL services/servers have differing criteria for what can get an IP listed or de-listed (removed) from their database. Examine your ctrl/dns_blacklist.cfg file to determine what DNSBL services your Synchronet Mail Server is using.
The Synchronet Mail Server can use DNS queries to multiple DNSBL servers (as configured in ctrl/dns_blacklist.cfg) for each inbound SMTP/ESMTP connection from a prospective mail transfer agent (MTA). If the MTA's IP address is listed by one of the DNSBL servers, then multiple actions may be taken:
- A Notice-level mail server log entry:
SMTP BLACKLISTED SERVER on ...(always) - An entry added to the
data/spam.logfile (always) - SMTP commands and lines of message headers and body text may be throttled at 1 line per second when the
DNSBL_THROTTLEoption is set - Reject the mail message, if the
DNSBL_BADUSERoption is set - Message Subject may be 'tagged' with a prepended configurable string (e.g.
SPAM:), seeDNSBlacklistSubjectsbbs.inikey - Message Header may be 'tagged' with a special header field (e.g.
X-DNSBL), seeDNSBlacklistHeadersbbs.inikey - Message may be received and ignored/dropped, if the
DNSBL_IGNOREoption is set - Message hash stored in a database of SPAM message body hashes (
data/spam.hash), if theDNSBL_SPAMHASHoption is set
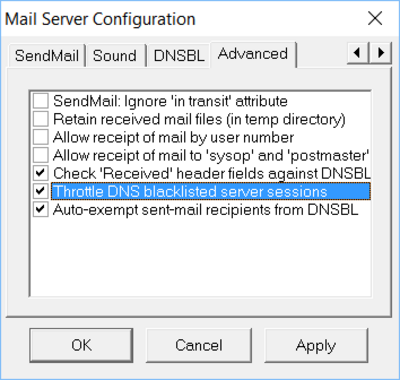
A mail message's “Received” headers may also be scanned for DNSBL-listed IP addresses (DNSBL_CHKRECVHDRS option) so that any e-mail messages that originate or pass-through a DNSBL-listed will be treated as though it is being delivered directly from a DNSBL-listed MTA.
When a DNSBL service reports an IP address as “black-listed”, any additional DNSBL services/servers are not queried.
Exemptions
MTA's whose IP address or hostname is listed in your ctrl/dnsbl_exempt.cfg file are never checked against DNSBL servers.
Mail from e-mail addresses that are listed in the dnsbl_exempt.cfg file are also exempt from DNSBL actions.
The destination addersses of email delivered by the Synchronet Mail Server's SendMail Thread are automatically added to your dnsbl_exempt.cfg file unless the NO_AUTO_EXEMPT option is set.
Synchronet Control Panel
External Mail Processors

SendMail
The Synchronet Mail Server's SendMail Thread is responsible for delivering Internet email using the SMTP or ESMTP protocols, optionally authenticating using PLAIN, LOGIN, or CRAM-MD5 SMTP-AUTH methods if required by an SMTP relay server.
Both Direct Delivery and Relaying (e.g. through intermediary mail server) is supported.
The SendMail Thread currently can service one outgoing SMTP/ESMTP session at a time.
The SendMail Thread will attempt to deliver securely (encrypted via TLS) when possible, though it will fall back to plain text delivery when necessary.
Post Office
The mail server also services authenticated “post office” requests from mail clients using the POP3 protocol, by default, on TCP port 110 and POP3S (Secure/encrypted POP3 over TLS) on TCP Port 995.
The POP3 server supports client authentication via the USER or APOP methods.
The POP3 server can service multiple simultaneous incoming sessions.
For IMAP support, see Deuce's IMAP Service.
Anti-SPAM
The Synchronet POP3 server will filter-out SPAM-tagged mail automatically when a POP3 client logs in with <username>#nospam.
Append “#nospam” to your login name/alias and any SPAM-tagged messages will not be listed/downloaded. This is useful if for example you use POP3 to download mail to your phone and have limited storage or sorting options. The SPAM-tagged messages will remain in your inbox on the BBS so you should use another POP3 or local mail client to download and delete those messages (which could potentially include false positives).
sbbs.ini
The [mail] section of the ctrl/sbbs.ini file supports the following configuration settings (key = value lines):
| Key | Default Value | Description |
|---|---|---|
| AutoStart | true | Automatically start up the server (manual is only supported in sbbsctrl) |
| Interface | [global] | Comma-separated list of IPv4 and IPv6 network interfaces to listen on for incoming SMTP/SMTPS connections |
| POP3Interface | Interface | Comma-separated list of IPv4 and IPv6 network interfaces to listen on for incoming POP3/POP3S connections |
| OutboundInterface | [global] | IPv4 network interface to use for outgoing SMTP/SMTPS connections (0.0.0.0 = any interface) |
| SMTPPort | 25 | TCP port number to listen on for incoming SMTP mail-delivery connections |
| SubmissionPort | 587 | TCP port number to listen on for incoming SMTP mail-submission connections |
| TLSSubmissionPort | 465 | TCP port number to listen on for incoming SMTPS (encrypted) mail-submission connections |
| POP3Port | 110 | TCP port number to listen on for incoming POP3 mail-retrieval connections |
| TLSPOP3Port | 995 | TCP port number to listen on for incoming POP3S (encrypted) mail-retrieval connections |
| MaxClients | 10 | Maximum number of simultaneous incoming TCP sessions supported |
| MaxConcurrentConnections | 0 | Maximum number of concurrent connections (without login) from the same IP address (0 = unlimited) |
| MaxInactivity | 120 | Maximum amount of TCP session inactivity before timeout and disconnection (in seconds) |
| MaxDeliveryAttempts | 50 | Maximum number of outbound mail delivery attempts before mail is bounced back to sender |
| RescanFrequency | 60M | Frequency (in seconds) of mail base re-scans for outbound mail to be sent/re-sent |
| SemFileCheckFrequency | 2 | Frequency (in seconds) of checks for semaphore files |
| LinesPerYield | 10 | Interval (in message body lines) of thread-yields during message receive (0 = none) |
| MaxRecipients | 100 | Maximum number of mail recipients for a single inbound SMTP mail message |
| MaxMsgSize | 20MB | Maximum size of incoming SMTP mail messages, in bytes |
| MaxMsgsWaiting | 100 | Maximum number of messages allowed in a (non-W-exempt) user's inbox |
| ConnectTimeout | 30 | Timeout (in seconds) before blocked outbound SMTP/TCP connections are aborted |
| HostName | [global] | Hostname of this server |
| TempDirectory | [global] | Directory to use for the storage of temporary files |
| RelayServer | Hostname or IP address of SMTP server to relay outbound mail through (requires RELAY_TX option) |
|
| RelayPort | 25 | TCP port number to connect with when relaying mail to RelayServer |
| RelayUsername | Username used to authenticate with RelayServer | |
| RelayPassword | Password used to authenticate with RelayServer | |
| DNSServer | <auto> | IP address of DNS server used to discover mail-exchange servers for outbound mail destinations |
| DefaultUser | Default recipient of mail for unrecognized recipient names (blank = none) | |
| DefaultCharset | Default MIME Content-Type charset value when unspecified (e.g. IBM437) |
|
| DNSBlacklistHeader | X-DNSBL | Header value to add to incoming mail messages from DNS-Blacklisted servers |
| DNSBlacklistSubject | SPAM | Word to insert into beginning of subject of mail messages from DNS-Blacklisted servers |
| POP3Sound | WAV file to play upon incoming POP3 connections (Windows only) | |
| InboundSound | WAV file to play upon incoming SMTP/SMTPS connections (Windows only) | |
| OutboundSound | WAV file to play upon outgoing SMTP/SMTPS connections (Windows only) | |
| NewMailNotice | “New e-mail from <%s>\r\n” | Format of telegram to send users upon receipt of incoming mail message |
| ForwardNotice | “and it was forwarded to: %s” | Additional telegram text to send to recipient of automatically forwarded mail |
| JavaScript* | [global] | JavaScript-related settings for external mail processing |
| LogLevel | [global] | Minimum severity of log messages to be displayed / stored |
| BindRetryCount | [global] | Maximum number of TCP port bind attempts before failure |
| BindRetryDelay | [global] | Delay (in seconds) between TCP port bind retries |
| LoginAttempt* | [global] | Failed login attempt throttling / filtering / banning |
| Options | ALLOW_POP3 | Mail server option flags (see below for details) |
Options
The Options key of the [mail] section of the ctrl/sbbs.ini file supports the following option flags (separated by a | character):
| Option | Description |
|---|---|
| USE_SUBMISSION_PORT | Support mail submissions on the SMTP submission port |
| TLS_SUBMISSION | Support incoming SMTP Submissions (encrypted) connections |
| ALLOW_POP3 | Support incoming POP3 connections for BBS users to use mail clients to retrieve the mail in their BBS inbox |
| DEBUG_POP3 | Log all POP3 activity (Debug log level) |
| TLS_POP3 | Support incoming POP3S (POP3/TLS) connections |
| DEBUG_TX | Log all transmissions (Debug log level) |
| DEBUG_RX_HEADER | Log headers of all received messages (Debug log level) |
| DEBUG_RX_BODY | Log body text of all received messages (Debug log level) |
| DEBUG_RX_RSP | Log all received responses (Debug log level) |
| ALLOW_RX_BY_NUMBER | Allow email to be received by user number in addition to name/alias (not recommended) |
| ALLOW_SYSOP_ALIASES | Allow email to received for various administrative aliases (e.g. “sysop”, “postmaster”) to be delivered to the sysop |
| NO_NOTIFY | Do not send telegrams to users notifying them of newly received email |
| NO_HOST_LOOKUP | Do not resolve/log hostnames of incoming TCP connections |
| USE_TCP_DNS | Use TCP instead of UDP for MX-record queries using DNS |
| NO_SENDMAIL | Do not send outbound Internet email |
| ALLOW_RELAY | Allow authenticated users to relay Internet email through this server |
| SMTP_AUTH_VIA_IP | Authenticate users via IP address when supported |
| DNSBL_REFUSE | Actively refuse all mail sessions from DNS-blacklisted servers |
| DNSBL_IGNORE | Ignore (silently-discard) mail from DNS-blacklisted servers |
| DNSBL_BADUSER | Block (report “invalid mailbox”) mail from DNS-blacklisted servers |
| DNSBL_CHKRECVHDRS | Check “Received” headers in mail messages for DNS-blacklisted servers |
| DNSBL_THROTTLE | Throttle mail sessions from DNS-blacklisted servers |
| DNSBL_SPAMHASH | Store hashes of confirmed SPAM messages for later comparison |
| SEND_INTRANSIT | Send mail that is marked 'in-transit' (not recommended) |
| RELAY_TX | Relay outbound SMTP mail through an intermediary SMTP RelayServer |
| RELAY_AUTH_PLAIN | When relaying mail to a RelayServer, use SMTP-PLAIN AUTH |
| RELAY_AUTH_LOGIN | When relaying mail to a RelayServer, use SMTP-LOGIN AUTH |
| RELAY_AUTH_CRAM_MD5 | When relaying mail to a RelayServer, use SMTP-CRAM_MD5 AUTH |
| NO_AUTO_EXEMPT | Do not automatically exempt outbound mail recipients in dnsbl_exempt.cfg |
| NO_RECYCLE | Do not allow this server to be automatically recycled by external event |
| KILL_READ_SPAM | Mark received SPAM messages for “Kill after read” |